You don’t notice how low your battery is until your screen goes black. At that moment, you were in the middle of a conversation in a group chat with some school friends. The bed frame creaks, and you sigh as you tug a charger from the opposite wall. Once it has been reconnected to a closer outlet, you lie back down and plug in your phone. A new message is waiting as soon as it turns on.
Curiously, this puts a smile on your face. Your past interactions with the sender have been positive, so you trust their name despite never seeing their face. Ignoring the ongoing conversation with your friends piling up in notifications at the top of the device, you turn your attention to this one message.
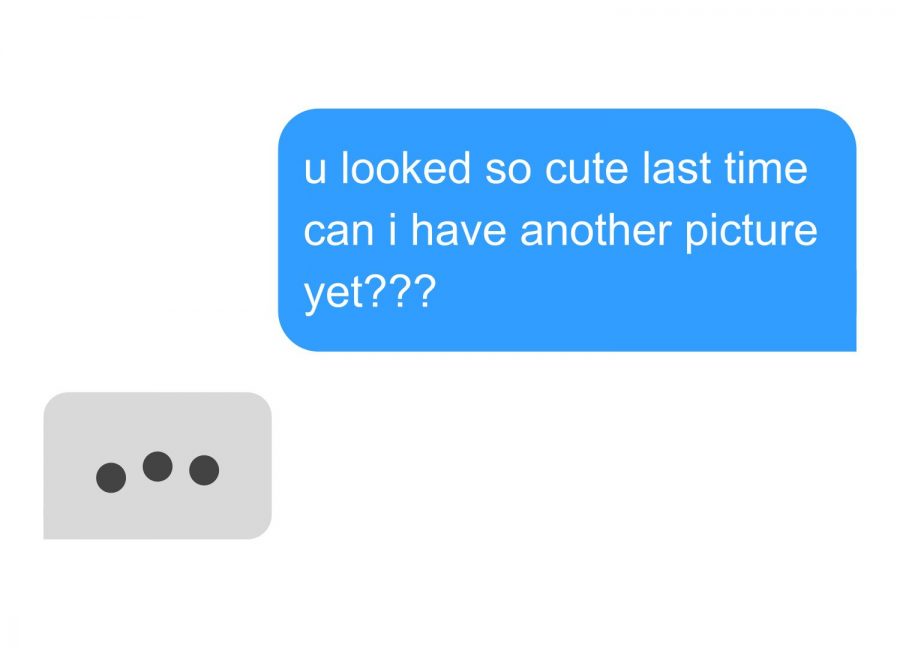
‘You looked so cute last time,’ it says. ‘Can I have another photo yet?’
You position the camera without a second thought.
Similar exchanges are commonplace on digital platforms.
For today’s youth, the internet is a fantastic playground. Although it lacks slides, monkey bars, and tanbark, it offers the same promise of fun, entertainment, and interaction. Online, however, anyone has the power to personalize their identity. Age and name are customizable account settings, and controversial statements are made inside brightly colored speech bubbles. Human authenticity is not a given, which is why stalking, pedophilia, grooming, scamming, sexual exploitation, and harassment run rampant on the internet, with victims suffering in equal measure.
For example, cyberharassment, more commonly known as cyberbullying, comes with little risk of bodily injury but overwhelmingly adverse effects on a victim’s psyche.
“Cyberbullying is an umbrella term for harmful online interactions,” Associate Marriage and Family Therapist (AMFT) Brooke Aguiar said. “Any social network or online platform can be used for it.”
In Aguiar’s own and other therapists’ experience, the interactions that fall under the category of cyberbullying are impersonation, cyberstalking, trickery, flaming (short but heated chat exchanges), and denigration (false information or pictures shared to negatively impact the individual’s reputation). Such exchanges exist on any platform that grants users the ability to converse, becoming increasingly common as technology becomes more accessible.
“The risk (of online harassment) is pretty much everywhere now, including online games and forums — this includes platforms that are meant for minors — anywhere with public servers,” AMFT Soy Kim said.
According to Kim, victims of cyberharassment can experience a plethora of negative effects, which commonly include hypervigilance, increased social anxiety, and challenges with sleep. The mental detriment that comes with being a victim of cyberharassment varies from person to person, but people can experience multiple or few effects at once or in different moments at any given time.
Socialization at this level of ease is a recent modern luxury and is both exciting and risky. Even if you have been harassed online by somebody you know, it is less challenging to take appropriate preventative action.
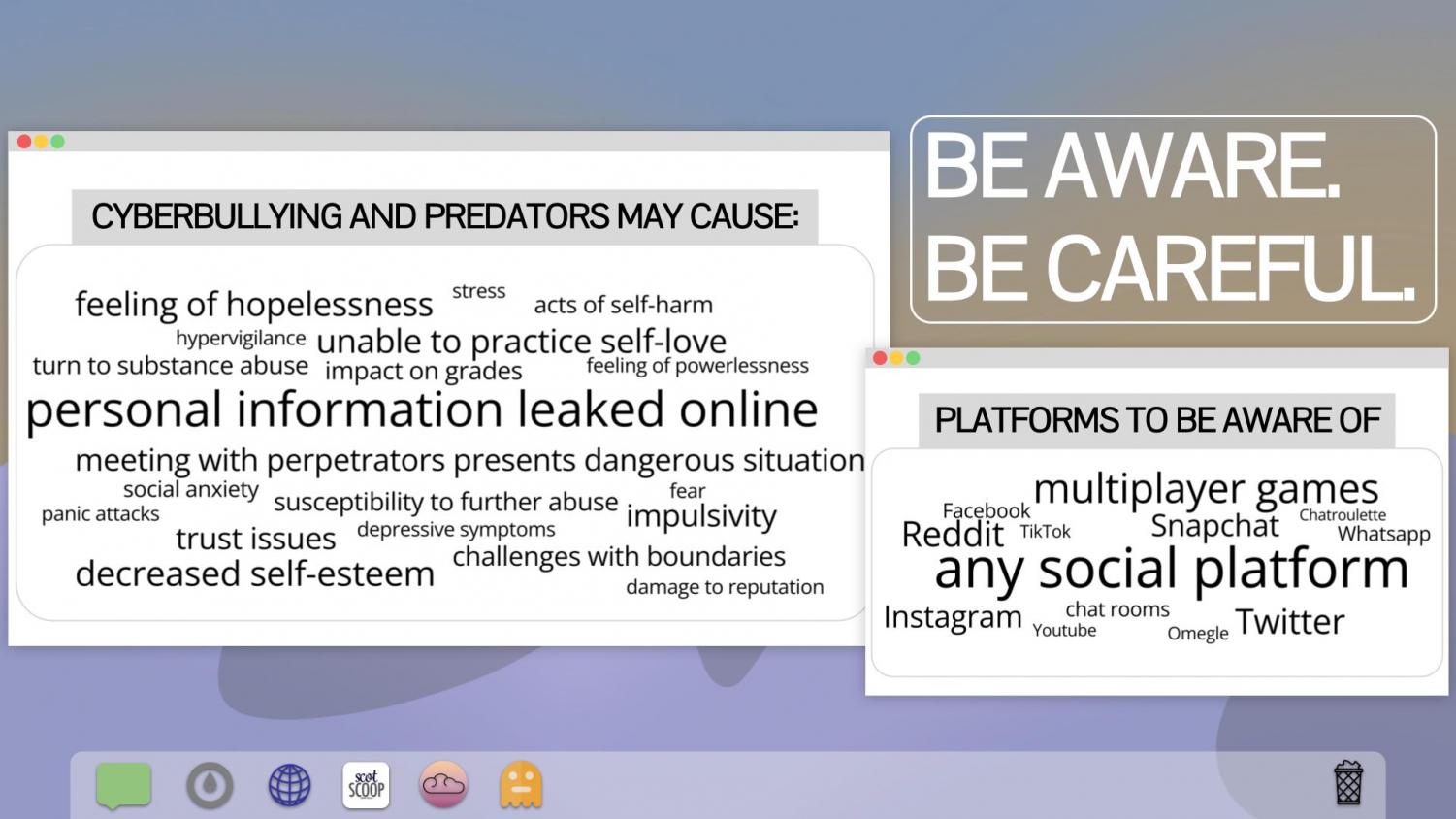
But what if it happens with a person you have never met, heard of, or talked to? Online, the young and vulnerable members of society find themselves frequent victims of the aforementioned cyberharassment as well as stalking, pedophilia, grooming, and sexual exploitation. While it remains common courtesy to act politely and cordially online, those with more malicious intentions have learned to swim with the current and feign friendliness to gain the trust of their targets. This process is known as grooming: a predatory process of befriending and establishing an emotional connection with a minor to later sexually abuse them, draw them into human trafficking, or take advantage of them in some other way.
Former sex crimes detective Tom Lee* has dealt with this reality firsthand. He and his associates used to pose as minors on Craigslist’s now-removed personals, responding to pedophilic ads put up by suspicious individuals.
“One thing that came as a shock to me was the ease at which I would get [predators] to come,” Lee said. “It wasn’t difficult to find them at all, nor was it difficult to get them to meet us.”
Lee’s department found great success initiating interactions with predators. Under the impression that the person on the other end was a minor in their early teens, perpetrators would show up at the designated meeting location, where they would often be arrested based on their intentions.
In a 2017 study, Sue Aitken, Danielle Gaskell, and Allen Hodkinson found that the grooming of females has no significant distinction from that towards male targets and is carried out through the motivation and capabilities of the offender and the offender’s ability to manipulate and control the victim. Through questioning perpetrators, Lee found that grooming minors did indeed depend on a predator’s capacity to appeal to a minor’s more vulnerable side.
“A lot of the time, they looked for young people from troubled homes, giving them attention and telling them things like, “you’re special.” When [a victim] hears that, they can’t help but think they aren’t a bad guy,” Lee said. That’s when [perpetrators] can turn on them. For example, maybe they meet first for a date. On the second meeting, they’ve been taken to a different county, stripped of their phone and any money they had, with no way to reach out for help.”
Predators even revealed that the grooming process was as simple as googling the phone number of a victim.
“Let’s say you were talking with a stranger on an anonymous messaging app. Thinking it’s not that big of a deal, you give them your phone number. If you Google a phone number, there’s a chance your general location or even your address can pop up,” Lee said. “These people might even be able to find out who your neighbors are and use that as an opening to gain your trust.”
Craigslist ads served as an example to Lee and his associates of predators who were upfront about sexual desire. In the context of soliciting sex, it was as simple as asking a child or teenager for a picture.
“Many of them try to get a minor to send a risky picture to them naked or something else compromising to keep them on the hook,” Lee said. “From there, they offer options: either send more pictures, or their picture is put up on the internet or sent to others. That’s the really interesting thing about this digital age, is once you put [personal information] out there, there’s no getting it back.”
Once a perpetrator has a piece of information or media that makes their target vulnerable, they blackmail them to comply with their demands. Lee recalls victims being dragged into a life of sex trafficking or having their lives ruined by private pictures made public online.
“Nowadays, people think that because they’re using a webcam or an app like Snapchat, which appears to delete photos, they think it is safe to send information that makes them vulnerable,” Lee said. “But say the receiver had another phone and could take a picture of that exchange. Basically, anyone can find a way to get around a restriction and use your information to harm you.”
Lee has personally encountered additional forms of virtual misconduct, such as scams. He asserted that any interaction with a stranger on the internet, regardless of outside factors, needs to be navigated with caution.
As a former detective, Lee offers a warning to those who choose to interact online.
“If you haven’t met them in real life, just assume they’re not who they are. Also, make sure to think about if you’re sending something you would be comfortable with others seeing,” he said. “If a perpetrator has taken advantage of you, remember that they have done it to someone else or will do it to someone else, so I encourage victims to make a report immediately.”
On the flip side, he advises online predators to consider the consequences of their actions. Possession of child pornography, internet solicitation of a minor, and stalking all carry serious repercussions, and the idea of complete safety being behind a screen is never guaranteed to any person participating in any exchange over the internet.
Nothing will change the fact that the internet remains an excellent source of news, knowledge, and entertainment. There is, and will always be, the risk of being a victim of cyberharassment, scamming, grooming, and the consequential destruction of physical, financial, and mental wellbeing.
It is of the utmost importance to be fully aware of the information you choose to put on the internet and the amount of trust you give to the people you meet on it.
Please, be safe at the playground.
*These names were changed by the author to protect their own and their colleagues’ identities in accordance with Carlmont Media’s anonymous sourcing policy.